Two basic approaches to packet switching are common: The most common is datagram switching (also known as a "best-effort network" or a network supporting the connection-less network service).This is what is used in the network layer of the Internet.
Datagram transmission uses a different scheme to determine the route through the network of links. Using datagram transmission, each packet is treated as a separate entity and contains a header with the full information about the intended recipient.
The intermediate nodes examine the header of a packet and select an appropriate link to an intermediate node which is nearer the destination. In this system, the packets do not follow a pre-established route, and the intermediate nodes (are known as "routers") do not require prior knowledge of the routes that will be used.
A datagram network is analogous to sending a message as a series of postcards through the postal system. Each card is independently sent to the final destination (using the postal system). To receive the whole message, the receiver must collect all the postcards and sort them into the original order. Not all postcards need be delivered by the postal system, and not all take the same length of time to arrive.
In a datagram network delivery is not guaranteed (although they are usually reliably sent). Enhancements, if required, to the basic service (e.g. reliable delivery) must be provided by the end systems (i.e. user's computers) using additional software. The most common datagram network is the Internet which uses the IP network protocol.
Applications which do not require more than a best effort service can be supported by direct use of packets in a datagram network (using the User Datagram Protocol (UDP) transport protocol). Such applications include Internet Video, Voice Communication, messages notifying a user that she/he has received new email, etc.
Most Internet applications need additional functions to provide reliable communication (such as end-to-end error and sequence control). Examples include sending email, browsing a web site, or sending a file using the file transfer protocol (ftp). This reliability ensures all the data is received in the correct order with no duplication or omissions. It is provided by additional layers of software algorithms implemented in the End Systems (A,D). Two examples of this are the Transmission Control Protocol (TCP), and the Trivial File Transfer Protocol (TFTP) which uses UDP.
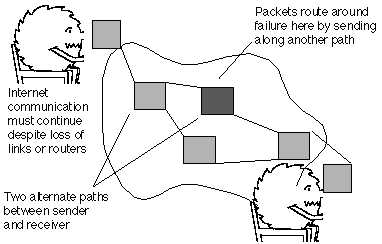
One merit of the datagram approach is that not all packets need to follow the same path (route) through the network (although frequently packets do follow the same route). This removes the need to set-up and tear-down the path, reducing the processing overhead, and a need for Intermediate Systems to execute an additional protocol.

Packets may also be routed around busy parts of the network when alternate paths exist. This is useful when a particular intermediate system becomes busy or overloaded with excessive volumes of packets to send. It can also provide a high degree of fault tolerance, when an individual intermediate system or communication circuit fails. As long as a route exists through the network between two end systems, they are able to communicate. Only if there is no possible way to send the packets, will the packets be discarded and not delivered. The fate (success/failure) of an application therefore depends only on existance of an actual path between the two End Systems (ESs). This is known as "fate sharing" - since the application shares the "fate" of the network.
There is another type of network known as a virtual circuit network. This has some advantages in particular scenarios. Although it is not covered as a part of the course, there is a web page comparing the two approaches.